EDS - what is it and who needs it
This is a digital analogue of a person’s signature - an electronic key.
Monitoring the integrity of a document, protecting it from forgery and modification, as well as confirming authorship are all functions of a signature. A form signed with an electronic signature has the same legal force as a traditional paper version. Digital details are obtained using cryptographic transformation of information. Advantages of digital signature:
- fast delivery of documents;
- the ability to automate the processing of necessary files;
- reduction of preparation and dispatch costs.
The scope of application of EDS is quite extensive: applying to state and municipal authorities (for example, the State Services website contains a catalog of services), participating in online auctions and receiving other commercial orders, tax reporting, filing claims in court. An electronic digital signature is also used when signing applications and letters by agreement with counterparties. An electronic signature for legal entities greatly simplifies document management.
Preparing the workplace for using an electronic signature
To participate in e-document flow, the user needs digital signature tools (keys and certificate) recorded on hardware media or in the OS registry, a licensed CIPF and plug-ins for correct operation in web browsers. The procedure for preparing and setting up a PC for working with digital signatures can be done independently or you can use the services of CA employees.
First of all, make sure that CIPF CryptoPro version no lower than 4.0 is installed on your PC. If not, install or update the program to the latest release.
Installation of the crypto provider is carried out on behalf of a user with administrator rights.
The next step is to install the key media driver, which can be downloaded for free on the manufacturer’s official website:
- Rutoken,
- eToken,
- JaCarta.
Without a driver, the computer will not “see” the USB drive, and the user will not be able to access the keys. Upon completion of the software installation, you must restart the PC.
- CryptoPro CSP 4.0
1 200 ₽
1200
https://online-kassa.ru/kupit/kriptopro-csp-4-0/
OrderMore detailsIn stock
- Cryptopro EDS
2 reviews
2 900 ₽
2900
https://online-kassa.ru/kupit/kriptopro-etsp/
OrderMore detailsIn stock
- CIPF CryptoPro CSP 4
1 review
1 200 ₽
1200
https://online-kassa.ru/kupit/skzi-kriptopro-csp-4/
OrderMore detailsIn stock
Installing certificates on PC
After installing the software, download the personal certificate of the digital signature owner to your PC:
- connect the USB token to the computer;
- through the control panel, find the CryptoPro CSP software;
- go to the “Service” page and click on the “View certificates in the container” button;
- using the “Browse” command, find the container (the line contains the name of the CA and the date of issue of the certificate), click “Ok” and “Next”;
- agree to the installation by pressing the “Install” button;
- if there is no button with an installation command, in the “Certificate for viewing” tab, go to “Properties” → “Install”;
- in the “Import Wizard” window, confirm the operation with the “Next” button;
- Check the box next to “Automatically select storage” and click “Finish”.
Upon completion of the procedure, a notification will appear stating that the SKPEP has been saved to the “Personal” folder.
There is another way to record a certificate on a PC. To do this, as in the first case, you need to find the CryptoPro program through the control panel and go to the “Service” section. Next, select the “Install personal certificate” command and follow the instructions of the Installation Wizard.
To view the certificates recorded on your PC, go through the control panel to the “CRYPTO-PRO” folder → “Certificates” → “Personal” and find the desired file by name.
To copy a certificate to another USB drive or PC, find the document in the “Personal” storage, go to the “Composition” tab → “Copy to file”. The private key is secret information, and to copy it along with the certificate, enter the password. After this, specify the location for copying and confirm the operation with the “Next” and “Finish” buttons. The file will be copied to the selected media.
After downloading your personal EDS, install the root certificate - a document confirming the accreditation of the CA that issued the EDS:
- go to SKPEP properties → “Certification path” tab;
- Left-click on the root file → “Install” and “Next”;
- Using the Browse command, find the Trusted Root Certification Authorities folder;
- Confirm saving with the “OK” button.
Browser settings
At the final stage, the certificate owner needs to configure the browser to work with the digital signature on Internet pages. Go to the “Products” section on the CRYPTO-PRO portal and download the free CryptoPro EDS Browser plug-in. The plugin is supported by all modern Internet browsers and OS. It is recommended to add sites with which you interact on a regular basis to the directory of trusted resources. To do this, through the Start menu, find CryptoPro CIPF and go to the plugin settings. On the "List of Trusted Sites" page, enter the addresses of all websites that accept a personal certificate from you.
Selecting a signature
| Type of signature | Description |
| Simple | Passwords, confirmation codes by e-mail, SMS are elements of a simple digital signature. It is actively used in online banking services using logins, passwords and one-time SMS to confirm transactions. With online insurance, it is used by the policyholder when filling out an application to purchase a policy. Authentication in information systems, receipt of government services, certification of documents within corporate electronic document management can also occur within the framework of using a simple type. |
| Unskilled reinforced (NEP) | Created as a result of cryptographic transformation of information. The NEP identifies the owner and also allows you to check whether changes were made to the file after it was sent. It consists of two keys, open and closed, which are stored on a special key carrier in the form of a USB key fob. NEP is required to participate in procurement under the contract system under 44-FZ as a supplier. The same type can be used for internal and external electronic document management, if the parties have previously agreed on this. |
| Qualified reinforced (KEP) | EPC is an electronic signature that gives documents legal force without additional conditions. It is created using cryptographic algorithms and is based on a public key infrastructure, but must have a qualified certificate approved by Order of the FSB of Russia No. 795 of December 27, 2011. CEP can only be issued by a certification center that is accredited by the Russian Ministry of Telecom and Mass Communications. CEP is needed to submit reports to regulatory authorities, participate as a supplier and customer in electronic auctions, work with government information systems, exchange formalized reports with the tax service, etc. |
General information about electronic signatures
Traditional paper documents are certified using a personal signature and seal. Digital signature is a tool that allows you to certify electronic documents (which include not only text files, but also graphic images, archives, and so on). An electronic signature is a set of metadata that can be used to establish the authorship and signer of a file. Such tools have existed literally since the 2000s and were initially introduced into the Windows operating families. Later, many states developed their own authentication mechanisms using digital signatures. In the Russian Federation, a similar system is now also working; many authorities already support working with electronic documents (with integration into the FSIS system).
Currently, work with digital signatures is regulated by Federal Law 63, the last amendments to which were made in 2015 . There is also a list of those signatures that can be used to sign documents, after which they acquire legal force.
According to the law, the following variations of digital signature are recognized in the Russian Federation:
- Simple. A simple login/password combination cannot be used for authorization on the websites of the State Services portal.
- Reinforced. They are a set of metadata with crypto encryption. They are analogous to the signature/seal combination on ordinary paper documents.
Only reinforced ones are suitable for working with FSIS, which in turn are divided into:
- unskilled;
- qualified.
Preparing documents
| Who applies | Documentation |
| Individual |
|
| Individual entrepreneur |
|
| Entity |
|
Remember that the certification center may ask for other documents to fully identify the key owner. For example, if necessary, when receiving an electronic digital signature, a power of attorney is provided to the individual entrepreneur.
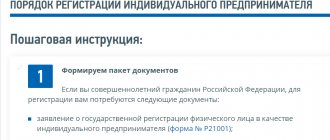
How to create an electronic signature, and what documents are needed for this
It is not at all difficult to obtain an electronic signature, and it is not a very long procedure. It is available to all legal entities, individual entrepreneurs, as well as individuals who, due to the nature of their activities, have decided to create an electronic signature. By submitting an application along with documents, in accordance with the requirements of the CA, and paying the cost of the service, anyone can receive the necessary tool for a simplified form of document flow.
To obtain a key certificate, an organization may need:
- Completed application form for the creation of an electronic signature;
- If the applicant is a legal entity, then it is necessary to provide a recent extract from the Unified State Register of Legal Entities (not more than thirty days old);
- Certificate of registration of the organization in the unified register of legal entities and certificate of registration with the tax service;
- If the electronic signature is made in the name of the head of the organization, it is necessary to provide a document (a copy of the order, certified by the seal of the organization and the signature of the head), giving him the right to act on behalf and in the interests of the company without a power of attorney;
- If the signature is made in the name of a representative of the organization, then a power of attorney will be required for him, with clearly defined powers;
- The person in whose name the electronic signature is issued must provide the original of his passport and a copy, as well as the original SNILS and a copy.
Even if the digital signature is prepared for the needs of an organization, the actual owner will still be an individual who has the right to sign from the organization.
For an individual entrepreneur, the set of documents will be slightly different:
- Completed application form for electronic signature;
- A certificate confirming the registration of the entrepreneur in the unified register, as well as registration with the Federal Tax Service inspection;
- A recent extract from the register of individual entrepreneurs, the issuance period should not be more than a month;
- The person in whose name the electronic signature is issued provides the original and a copy of the passport and SNILS.
Individuals provide the CA with: an application to create a signature, as well as their own passport and SNILS.
Selecting a certification center
The question of how to create an electronic signature falls within the competence of certification institutions. If you receive an NEP, you can contact any territorially suitable center. However, upon receipt of the CEP, only accredited institutions issue it. The Ministry of Communications of the Russian Federation, as a federal executive body authorized in the field of using digital signatures, carries out accreditation of certification centers (Article 16 63-FZ). The list of centers that are currently accredited is available on the website of the Ministry of Telecom and Mass Communications. It is updated regularly, so it is better to get the current version there.
An electronic signature for individual entrepreneurs, as well as for individuals and legal entities, is produced on average within 2 days. You can buy an electronic digital signature in the range from 3,000 to 8,000 rubles, depending on the type, and for an additional fee, expedited production within several hours is provided.
Business Solutions
- shops clothing, shoes, groceries, toys, cosmetics, appliances Read more
- warehouses
material, in-production, sales and transport organizations Read more
- marking
tobacco, shoes, consumer goods, medicines Read more
- production
meat, procurement, machining, assembly and installation Read more
- rfid
radio frequency identification of inventory items More details
- egais
automation of accounting operations with alcoholic beverages Read more
What does the digital signature look like? This is a short cipher - alphabetic, digital, symbolic. When encrypting, completely different characters in different quantities can be used, so it is not possible to say in advance. It is usually sent by email. An access key is also obtained.
EP has its own expiration date, usually 1 year. This limitation is due to the fact that fraudulent transactions are often allowed and hacking attempts occur - not always successful, but still. Then you should buy a new one or extend the term of the previous cipher, but get a new key and certificate - this is provided in a single form and is stored exclusively with the head of the department, the head of the company, or with a specific individual owner, if we are talking about digital signature for home use.
The service is a paid service, and the cost may vary depending on what features are included in the package. But a standard, minimum contract will cost an individual an average of 700 rubles. Sometimes you can get it for free, in cases where the simplest option is enough (we'll talk more about the types a little later). Why do individuals obtain an electronic signature?
- sign documents while at home, at work, while traveling – wherever there is Internet access;
- use online services that are widely available throughout the civilized world, but in Russia are often not yet very developed;
- do not go to different authorities to sign using the classic method, that is, do not spend a lot of time communicating with people with whom you have no desire to communicate.
This service is sometimes called a seal because it provides similar legal certainty. The main content is digital, so storage occurs on a medium, most often on a USB flash drive, which entrepreneurs, like individuals, must carry with them. Inside there are files that contain:
- An identifying certificate is the code itself, a cipher that your opponents in electronic document management will see. In fact, this is the seal itself.
- Private and public keys - with their help, only you can make any changes to the document. This can be compared to writing your initials in pen under each page of a contract so that you can't write additional terms later.
You can receive such a package on a flash drive only at certification centers accredited by the state. They do not give repeating meanings, only individual combinations for each applicant. If the code is lost or stolen, you must immediately contact the police, because until the application is submitted and the seal is temporarily frozen, all documents signed in this way will be considered valid, even if the fraudster has thus “signed over” your house or sold your car.
To summarize the first introductory section, let’s say that the presence of an electronic signature significantly simplifies document flow and expands the range of possible actions before a person.
The history of the emergence of electronic signatures for individuals
The pair of cipher and key has been used since time immemorial - this is how doves or messengers were sent, encryption was used by both military leaders and lovers who did not want to make their relationship public. But the nuance, which is also a significant disadvantage, is that you need to simultaneously transmit both the message and the decryption key. But already in the second half of the 20th century, this problem was solved by cryptographers Jiff and Hellman, who proposed messaging to determine a single key, or rather, there should be two of them - for encryption (it can be open) and for decryption, of course, private. This allows information to be transmitted in such a way that if intercepted, the veneer will not be able to understand anything without the second half of the riddle.
Over time, such encryption systems were actively used to preserve political and military confidential data. Then the same technique moved into the sphere of commercial relations, for example, it was adopted in order to maintain all banking transactions with each of its clients. With the development and improvement of electronic document management, technology passed into the hands of legal entities, and then individuals.
How to issue and where to obtain an electronic signature for the chief accountant
What could be the procedure for obtaining an electronic signature by the chief accountant of an enterprise? In this case, it is better to use the first option - when a separate signature is issued for the employee. This is due precisely to the fact that many documents in the company must be signed by the chief accountant.
The chief accountant of the company, if a decision is made to vest him with the appropriate powers and issue a separate digital signature for him, will have to present to the certification center the same documents as the director - but only instead of the order presented by the director, he needs to show a local administrative document about vesting the accountant with the necessary powers to use digital signatures.
Qualified electronic digital signature (CED): what is it?
Law No. 63-FZ defines 3 types of electronic signatures:
- simple,
- reinforced,
- reinforced qualified.
See also “What is a non-qualified electronic signature”.
A simple digital signature performs only one of the above functions - it certifies the fact that a document has been signed by a specific person. However, its resistance to decryption is, as a rule, not too high. An example of a simple digital signature is the password to a person’s email, from which he sends his messages, “in a simple way” certifying the fact that they belong to him. Email passwords rarely exceed a dozen characters, which is incomparable with the 512-bit encryption depth according to GOST R 34.10-2012. In addition, someone else may accidentally or intentionally recognize them.
In turn, the enhanced digital signature is encrypted much deeper than the e-mail password - in principle, 512-bit encryption characterizes the enhanced signature. Finding out it, like a password for an e-mail, is extremely difficult, since it is a sequence of computer data: firstly, well encrypted, and secondly, not intended to be presented in a text form understandable to humans.
The qualification of an electronic signature is a guarantee of its maximum resistance to decryption from the point of view of a particular state standard. In the case of Russian digital signatures, their qualification is compliance with the requirements of GOST R 34.10-2012. Only those electronic signatures that meet the requirements of this standard can be recognized as qualified.
ConsultantPlus experts explained how a legal entity can obtain an enhanced qualified electronic signature. Get trial access to the K+ system and upgrade to the Ready Solution for free.
It is not at all necessary that a regular enhanced signature will be less protected from hacking than a qualified one. It is quite possible that the encryption standards that are implemented in an unqualified digital signature, developed, for example, by a private research center, will be even more stringent than according to GOST R 34.10-2012.
The use of enhanced qualified digital signature may be prescribed by separate regulations. For example, to send reports to government agencies, Russian companies must use the EPC. In turn, those types of CEPs that are adapted for working with specific documents, for example, tax reporting forms, are not suitable for organizing the exchange of documents between enterprises.
Anyone can use a simple electronic signature - for example, through their e-mail or mobile number. In order to use the enhanced one, you will need to use one of its mandatory components - a certificate. Let's take a closer look at its features.
How to create an electronic signature and not violate the rules for storing electronic documents
The validity period of an electronic signature certificate is one year , and this period is shorter than the retention period of most documents. To correct this situation, there is a time stamp - it replaces the date on the document and confirms that the electronic signature certificate had full legitimacy when signed.
You can find out whether the certificate is valid at the time of signing on the official website of the CA, which necessarily posts a list of revoked invalid certificates.
Electronic documents themselves, signed by electronic signature, can be stored in two ways :
- Local storage (on a hard drive, on an organization’s server, removable media);
- Storage in the cloud (on the server of the organization that provided you with this service, use is possible if there is available Internet traffic).